In 2024, the landscape of cyber threats targeting operational technology (OT) systems showed concerning trends, particularly in cyber attacks that resulted in physical consequences. While the overall increase in cyber incidents impacting OT was not as steep as in previous years, the nature of these attacks, their scale, and the players behind them are evolving rapidly.
The data in the Waterfall / ICS Strive 2025 OT Threat Report shows how the threat environment has changed, and the analysis sections offer food for thought as organizations evaluate their defenses against the evolving environment.
A Significant Surge in Attacks with Physical Consequences
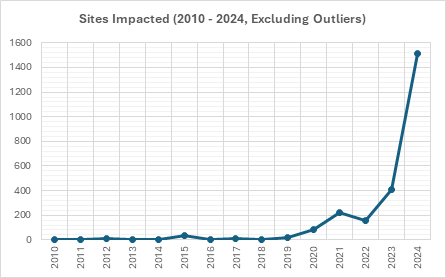
In 2024, there was a significant increase in the number of physical sites where production was impaired. The number of affected sites more than doubled, a 146% increase in 2024 over 2023—going from 412 sites in 2023 to 1,015 in 2024. Most attacks are not isolated events; most cause physical consequences at multiple physical locations.
Escalating Nation-State Threats
Attacks by nation-state threat actors tripled in 2024 over 2023. The numbers involved are still small, but the trend is disturbing, for more than one reason. Unlike cybercriminals who seek financial gain through ransomware attacks and very often cause physical consequences only “accidentally,” many nation-state and most hacktivist actors deliberately work to bring about physical consequences in attacks on critical industrial infrastructures. Furthermore, all nation-state attacks in the report are driven by kinetic warfare in three regions: the Russia-Ukraine war, the Israel-Iran conflict, and the ongoing tensions between Western democracies and China.
Transportation and Manufacturing: Key Targets
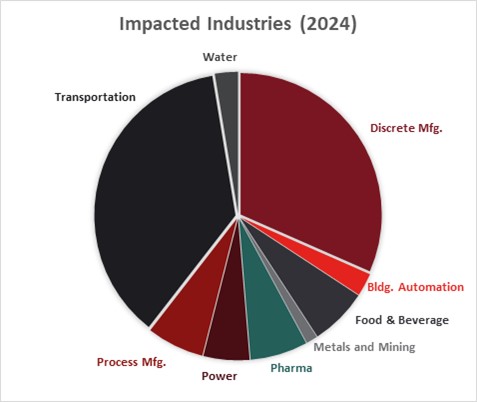
The transportation sector continues to bemost affected by cyber attacks with physical consequences, representing 37% of all incidents in 2024. Discrete manufacturing remains another top target. Together, these two sectors make up nearly 70% of attacks with physical consequences. Neither industry has a reputation for strong cybersecurity programs, and both industries tend to see far greater interconnectedness and interdependency of IT and OT networks than do the average power transmission or transmission utility for example. This interconnectedness is a well-known source of vulnerability.
The Role of Ransomware and the Rise of ICS/OT Malware
Ransomware continues to be a significant driver of cyber attacks in the OT space, and it’s clear from the report that the impact of ransomware on OT systems has not diminished. 2024 also saw a concerning increase in the rate of discovery of malware specifically designed for Industrial Control Systems (ICS) and OT environments. Three new strains of such malware were discovered in 2024, while only six were discovered in the preceding fourteen years of our data set. The numbers are still small, but again, the trend is concerning.
ICS/OT-specific malware variants can really have only one purpose. The increased rate of discovery suggests that state-sponsored actors are increasing their focus on bringing about physical consequences, a shift that may lead to more severe disruptions in the future.
Conclusion: A Call to Action
These and many other data points and analyses are in the report. As defenders we all have a responsibility to address credible threats to our operations, especially threats with a real chance of bringing about unacceptable physical and other consequences.
Ransomware continues to be a pervasive threat to all businesses and to physical operations. When it comes to nation states, it is reasonable to assume that the threat actors observed in 2024 used the simplest, cheapest, least-capable tools they needed to use in order to achieve their mission objectives. It is almost certain that these threat actors have more capable tools and techniques than they have revealed thus far in the public sphere.
To project our adversaries’ capabilities into the future, it is important to understand what those adversaries have revealed recently. The Waterfall / ICS Strive threat report is the most credible report in the industry – the entire data set for the report back to 2010 is public and is included in Appendix A of the report. I encourage all defenders to read the report and reflect on what the data means for the future of the OT security threat environment.



